In this post, I will setup security on Oracle BDSG (Big Data Spatial and Graph). Note that Oracle BDSG is a licensed software. Please, consult product documentation and vendor before using it for non-personal/non-development use cases.
Here are some references related to configuring security on BDSG :
https://docs.oracle.com/en/bigdata/big-data-spatial-graph/3.0/bdspa/using-in-memory-analyst.html#GUID-26963C28-3672-404B-A66B-7F6CBC2B1D93
https://docs.oracle.com/cd/E56133_01/latest/reference/config/server.html#authentication-and-roles
As written in references, clients can be authenticated and authorized using two-way SSL/TSL. There are 2 types of users with pre-defined privileges: USER and ADMIN. There is no detailed information about the differences between these two user types but it seems that only ADMIN can use oracle.pgx.api.admin java package. Here is the link to the product javadocs where fields and methods of this package can be seen:
https://docs.oracle.com/cd/E56133_01/latest/javadocs/index.html
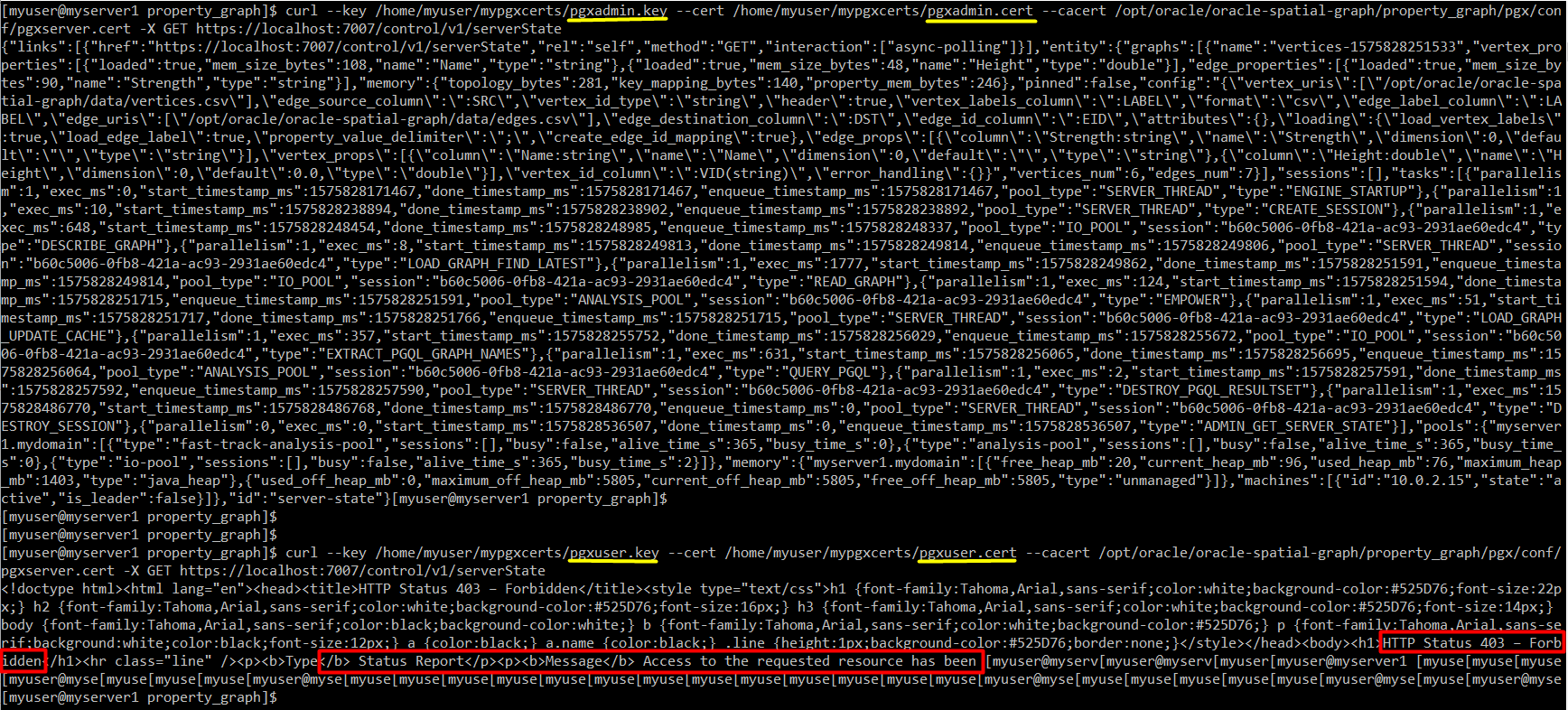
For example, when I query serverstate using REST API with USER privilege, I get following error:
curl –key /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxuser.key –cert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxuser.cert –cacert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert -X GET https://localhost:7007/control/v1/serverState
Message Access to the requested resource has been denied
Description The server understood the request but refuses to authorize it.
Setting up certificates
For authentication, first we will create certificates for
- PGX Server (pgxserver)
- A client certificate for non privileged user (pgxuser)
- A client certificate for privileged user (pgxadmin)
I will use self-signed certificates. However, it is recommended to use CA signed certificates for production. Also notice that I am adding dns:localhost and ip:127.0.0.1 as “Subject Alternative Name” extension to my certificates to avoid certification validation error while working locally.
keytool -genkey -alias pgxserver -keyalg RSA -storetype PKCS12 -keystore pgxserver.p12 -ext SAN=dns:localhost,ip:127.0.0.1
keytool -genkey -alias pgxuser -keyalg RSA -storetype PKCS12 -keystore pgxuser.p12 -ext SAN=dns:localhost,ip:127.0.0.1
keytool -genkey -alias pgxadmin -keyalg RSA -storetype PKCS12 -keystore pgxadmin.p12 -ext SAN=dns:localhost,ip:127.0.0.1
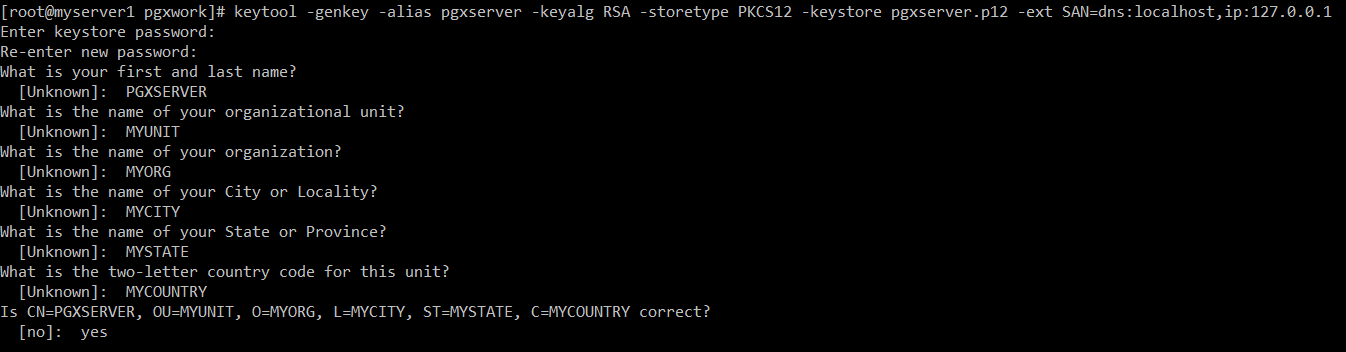
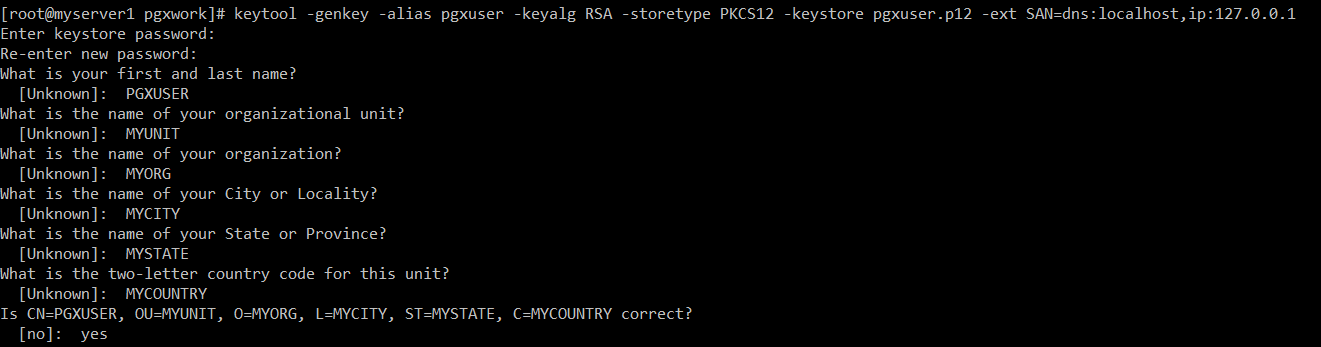
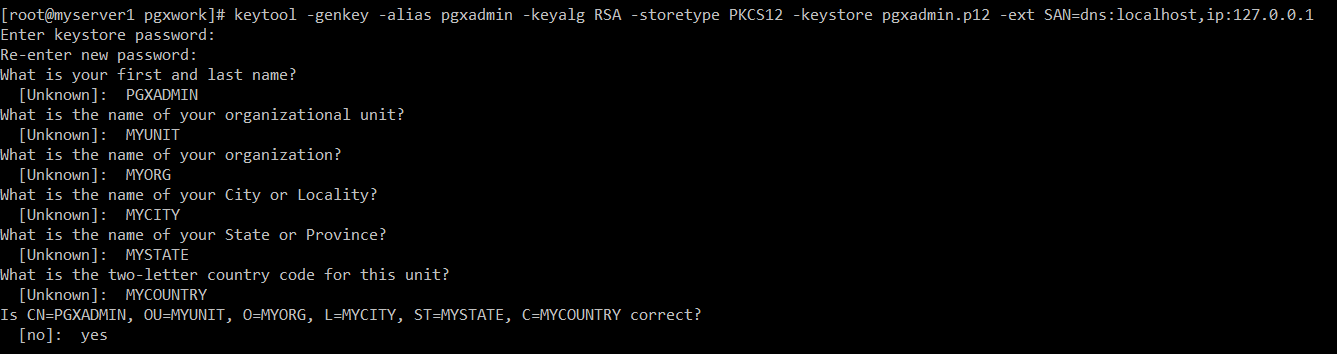
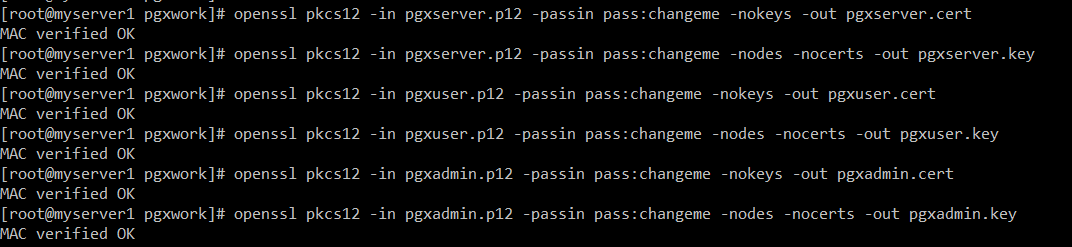
Let’s create PEM certificates and keys. They are for client applications like curl. I am not setting password for PEM keys. However, in a production environment you may consider protecting keys with password.
openssl pkcs12 -in pgxserver.p12 -passin pass:changeme -nokeys -out pgxserver.cert
openssl pkcs12 -in pgxserver.p12 -passin pass:changeme -nodes -nocerts -out pgxserver.key
openssl pkcs12 -in pgxuser.p12 -passin pass:changeme -nokeys -out pgxuser.cert
openssl pkcs12 -in pgxuser.p12 -passin pass:changeme -nodes -nocerts -out pgxuser.key
openssl pkcs12 -in pgxadmin.p12 -passin pass:changeme -nokeys -out pgxadmin.cert
openssl pkcs12 -in pgxadmin.p12 -passin pass:changeme -nodes -nocerts -out pgxadmin.key
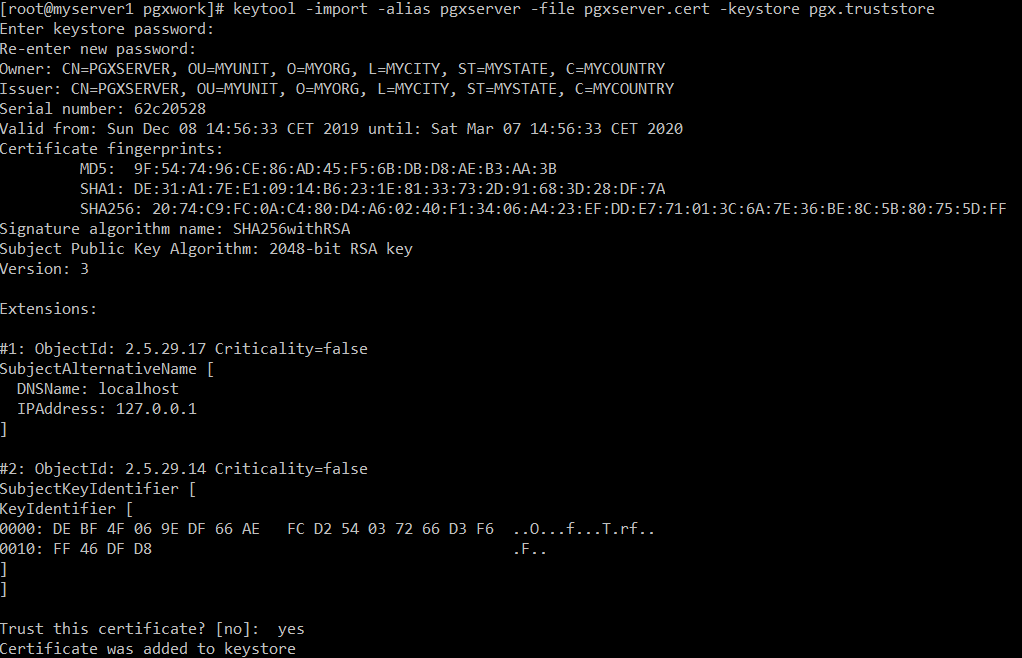
Let’s create a trust-store using all certificates so clients and server will be able to validate each other.
keytool -import -alias pgxserver -file pgxserver.cert -keystore pgx.truststore
keytool -import -alias pgxuser -file pgxuser.cert -keystore pgx.truststore
keytool -import -alias pgxadmin -file pgxadmin.cert -keystore pgx.truststore
Finally, let’s create jks key-stores for clients
keytool -importkeystore -srckeystore pgxuser.p12 -destkeystore pgxuser.jks -srcstoretype PKCS12 -deststoretype jks -srcstorepass changeme -deststorepass changeme -srcalias pgxuser -destalias pgxuser -srckeypass changeme -destkeypass changeme
keytool -importkeystore -srckeystore pgxadmin.p12 -destkeystore pgxadmin.jks -srcstoretype PKCS12 -deststoretype jks -srcstorepass changeme -deststorepass changeme -srcalias pgxadmin -destalias pgxadmin -srckeypass changeme -destkeypass changeme
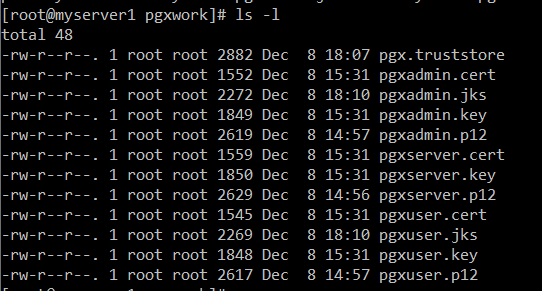
Now, we have all these:
We continue with setup SSL/TLS and authorization configuration in PGX server.
cp pgxserver.cert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert
cp pgxserver.key /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.key
cp pgxadmin.cert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxadmin.cert
cp pgxuser.cert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxuser.cert
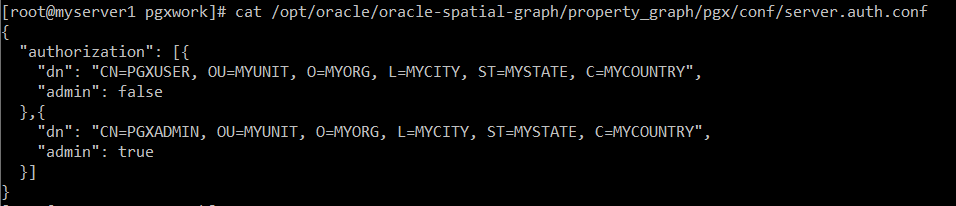
{
"authorization": [{
"dn": "CN=PGXUSER, OU=MYUNIT, O=MYORG, L=MYCITY, ST=MYSTATE, C=MYCOUNTRY",
"admin": false
},{
"dn": "CN=PGXADMIN, OU=MYUNIT, O=MYORG, L=MYCITY, ST=MYSTATE, C=MYCOUNTRY",
"admin": true
}]
}
{
"port": 7007,
"enable_tls": true,
"enable_client_authentication": true,
"server_cert": "/opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert",
"server_private_key": "/opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.key",
"ca_certs": [
"/opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert",
"/opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxuser.cert",
"/opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxadmin.cert"
],
"authorization": "server.auth.conf",
"working_dir": "../tmp_data"
}
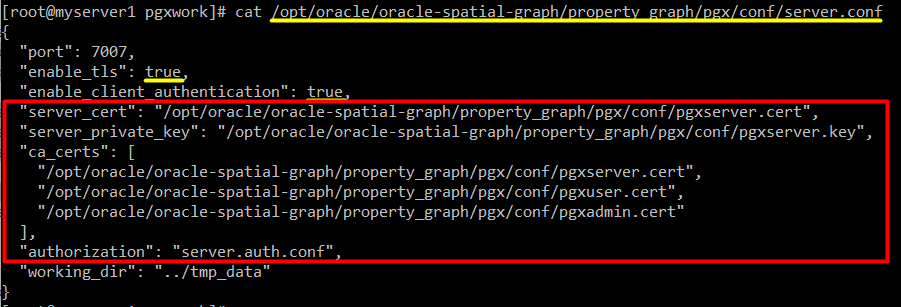
I will copy necessary client certificates to a non-root account in order to execute pgx client with a regular Linux user.
mkdir /home/myuser/mypgxcerts
cp pgx.truststore /home/myuser/mypgxcerts/
cp pgxadmin.cert /home/myuser/mypgxcerts/
cp pgxadmin.jks /home/myuser/mypgxcerts/
cp pgxadmin.key /home/myuser/mypgxcerts/
cp pgxuser.cert /home/myuser/mypgxcerts/
cp pgxuser.jks /home/myuser/mypgxcerts/
cp pgxuser.key /home/myuser/mypgxcerts/
chown -R myuser:myuser /home/myuser/mypgxcerts
Start server:
cd /opt/oracle/oracle-spatial-graph/property_graph
./pgx/bin/start-server
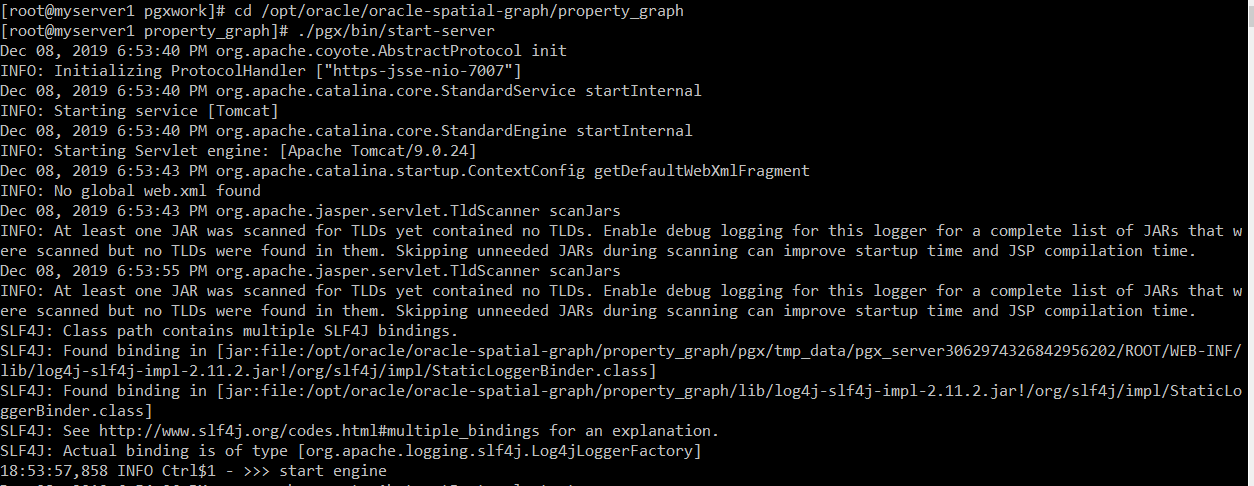
From another terminal, connect as client and test:
su – myuser
cd /opt/oracle/oracle-spatial-graph/property_graph
JAVA_OPTS=’ -Djavax.net.ssl.keyStore=/home/myuser/mypgxcerts/pgxuser.jks -Djavax.net.ssl.keyStorePassword=changeme -Djavax.net.ssl.trustStore=/home/myuser/mypgxcerts/pgx.truststore -Djavax.net.ssl.trustStorePassword=changeme’ bin/opg –base_url=https://localhost:7007
loadedGraph = session.readGraphFiles(“/opt/oracle/oracle-spatial-graph/data/vertices.csv”,”/opt/oracle/oracle-spatial-graph/data/edges.csv”,”LoadedGraphName”)
loadedGraph.queryPgql(“SELECT * MATCH (n) -[e]- (m)”).print(10).close()
su – myuser
cd /opt/oracle/oracle-spatial-graph/property_graph
JAVA_OPTS=’ -Djavax.net.ssl.keyStore=/home/myuser/mypgxcerts/pgxadmin.jks -Djavax.net.ssl.keyStorePassword=changeme -Djavax.net.ssl.trustStore=/home/myuser/mypgxcerts/pgx.truststore -Djavax.net.ssl.trustStorePassword=changeme’ bin/opg –base_url=https://localhost:7007
loadedGraph = session.readGraphFiles(“/opt/oracle/oracle-spatial-graph/data/vertices.csv”,”/opt/oracle/oracle-spatial-graph/data/edges.csv”,”LoadedGraphName”)
loadedGraph.queryPgql(“SELECT * MATCH (n) -[e]- (m)”).print(10).close()
To test the user/admin authorization difference, test following two curl commands. While the one run with admin gets the metrics, the other gets permission error:
--admin
curl --key /home/myuser/mypgxcerts/pgxadmin.key --cert /home/myuser/mypgxcerts/pgxadmin.cert --cacert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert -X GET https://localhost:7007/control/v1/serverState
--user
curl --key /home/myuser/mypgxcerts/pgxuser.key --cert /home/myuser/mypgxcerts/pgxuser.cert --cacert /opt/oracle/oracle-spatial-graph/property_graph/pgx/conf/pgxserver.cert -X GET https://localhost:7007/control/v1/serverState